A Reflective Attack Can Be Increased in Intensity by Combining It With What Type of Attack?
![]()
Whatsoever attack, regardless of form, endangers the availability of your infrastructure, resulting in disrupted or failed service to users and customers. Our gratis Anti-DDoS protection ensures your infrastructure remains accessible 24/7 through a network capacity of 20+ Tbps and a combination of mitigation techniques, including packet analysis, packet mitigation, and server traffic vacuuming. Read on to acquire more almost our VAC engineering science based mitigation solution.
| Free Anti-DDoS protection | Anti-DDoS GAME | |
|---|---|---|
| Free Anti-DDoS protection | Anti-DDoS GAME | |
| Related products | Hosted Private Cloud, Defended Servers | Dedicated Game Servers |
| Number of attacks per month | Unlimited | Unlimited |
| Gbps limit of attack | Unlimited | Unlimited |
| Duration of attacks per calendar month | Unlimited | Unlimited |
| Type of assault | All | All |
| Detection and Auto-Mitigation | ✔ | ✔ |
| Multi-bespeak Mitigation | Europe (RBX, GRA, SBG, WAW, LIM, ERI) North America (WAS, BHS(BHS) Asia (SGP, SYD) | Europe (RBX, GRA, SBG, WAW, LIM, ERI) N America (WAS, BHS(BHS) Asia (SGP, SYD) |
| Permanent mitigation | ✔ | ✔ |
| Two-fashion mitigation | - | ✔ (L3/L4/L7) |
| 12 Tbps of boosted network | ✔ | ✔ |
| Network Firewall | Configurable | Configurable |
| Shield | ✔ | ✔ |
| Armor | ✔ | Customizable |
| API v6 | ✔ | ✔ |
| Manager v6 | ✔ | ✔ |
| Support | Mailing listing | Mailing list |
Understanding DDoS
What is a DDoS set on?
Businesses of all sizes, in any industry are vulnerable to distributed denial of service (DDoS) targeting unless they leverage the right applications to secure confronting attack.
A DDoS attack aims to render a server, service, or an infrastructure unavailable by overloading the server'southward bandwidth or monopolizing its resources to the signal of depletion. During a DDoS assail, a multitude of requests are sent simultaneously from multiple points across the cyberspace. The intensity of this "crossfire" renders the service unstable, or fifty-fifty worse, unavailable.
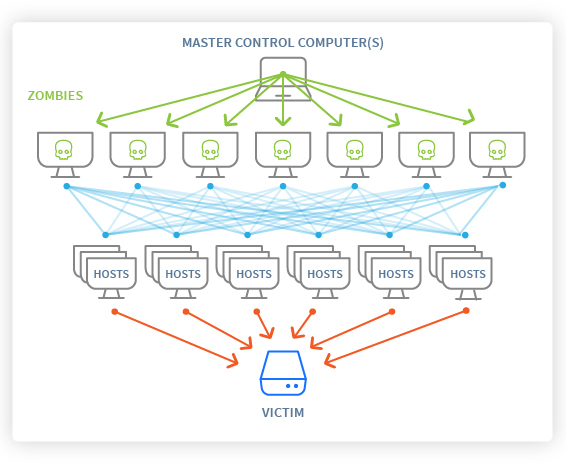
At that place are three major ways DDoS attacks brand your site, server, or infrastructure unavailable:
Bandwidth: this type of set on consists of saturating the server's network chapters, rendering information technology unreachable.
Resources: this type of set on consists of depleting the machine's organisation resources, which prevents information technology from responding to legitimate requests.
Exploitation of Software Fault: too chosen "exploit", this blazon of set on targets a item software fault either to make the machine unavailable or to take command of it.
| Name of Attack | Blazon of Attack | OSI level | Explanation of attack principle |
| Name of Attack | Blazon of Attack | OSI level | Explanation of set on principle |
| SMURF | Bandwidth | L3 | ICMP broadcast attack usurping the source address to redirect multiple responses to the victim |
| TCP SYN ACK Reflection Flood | Bandwidth | L4 | Mass sending of TCP connections requests to a large number of machines, usurping the victim'south source address. The bandwidth of the victim will exist saturated by the responses to these requests |
| UDP Inundation | Bandwidth | L4 | Mass sending of UDP packets (not requiring a previously-established connexion) |
| Distributed DNS Amplification Attack | Bandwidth | L7 | Mass sending of DNS requests usurping the source accost of the victim, to a large number of legitimate servers. As the response is more voluminous than the question, an distension of the set on follows |
| ICMP Echo Request Inundation | Resource | L3 | Too chosen "Ping Flood, mass sending of packets including the response of the victim, which has the same content as the original packet |
| IP Packet Fragment Set on | Resources | L3 | Sending of IP packets that voluntarily reference other packets that volition never be sent, which saturates the victim's memory |
| IGMP Overflowing | Resource | L3 | Mass sending of IGMP packets (multi-bandage management protocol) |
| TCP SYN Overflowing | Resources | L4 | Mass sending of TCP connections requests |
| TCP Spoofed SYN Alluvion | Resource | L4 | Mass sending of TCP connections requests to usurp the source address |
| TCP ACK Flood | Resources | L4 | Mass sending of TCP segment delivery receipts |
| TCP Fragmented Attack | Resource | L4 | Sending of TCP segments that voluntarily reference other segments that will never be sent, which saturates the victim'south retentiveness |
| UDP Fragment Flood | Resource | L4 | Sending of UDP datagrams that voluntarily reference other datagrams that will never be sent, which saturates the victim's retention |
| DNS Flood | Resources | L7 | Attack of a DNS server by mass sending of requests |
| HTTP(S) GET/POST Inundation | Resources | L7 | Attack of a web server by mass sending of requests |
| Ping of Death | Exploit | L3 | Sending of ICMP packets which exploit an implementation bug in certain operating systems |
Managing DDoS attacks
Phase 1: The server is operational – no assault
Net-based services are used without any problem. The traffic passes through the backbone of our network then arrives at the information center. Finally, it is handled by the server that sends back the responses over the internet.
Phase 2: The DDoS set on begins
The attack is launched via the cyberspace and on the courage. Given the surplus capacity of the bandwidth on the backbone, the attack will not cause saturation on any link. The attack reaches the server, which begins to handle the initial attack. At the same time, analysis of the traffic flags that an attack is underway and triggers the mitigation.
Stage 3: Mitigation of the set on
Between 15 and 120 seconds after the attack has begun, mitigation is automatically activated. Incoming server traffic is vacuumed by the iii VACs, with a total chapters of 480 Gbps (3x 160 Gbps) of mitigation, hosted in 3 OVH information centers. The assault is blocked with no elapsing or size limit, regardless of type. Legitimate traffic passes through the VAC and arrives at the server. The server responds directly without going back through the VAC. This process is called auto-mitigation.
Stage 4: Finish of the assault
Generating an assault is costly, and even more then when information technology is ineffective. Later on a certain time has passed, the attack will come to an end. Car-mitigation is maintained for 26 hours later on the attack has ended. This ways whatever new attack that occurs inside a few minutes, a few hours, or 24 hours will be blocked. Subsequently only 26 hours, auto-mitigation is disabled but remains gear up to be reactivated upon detection of a new attack.
Anti-DDoS protection
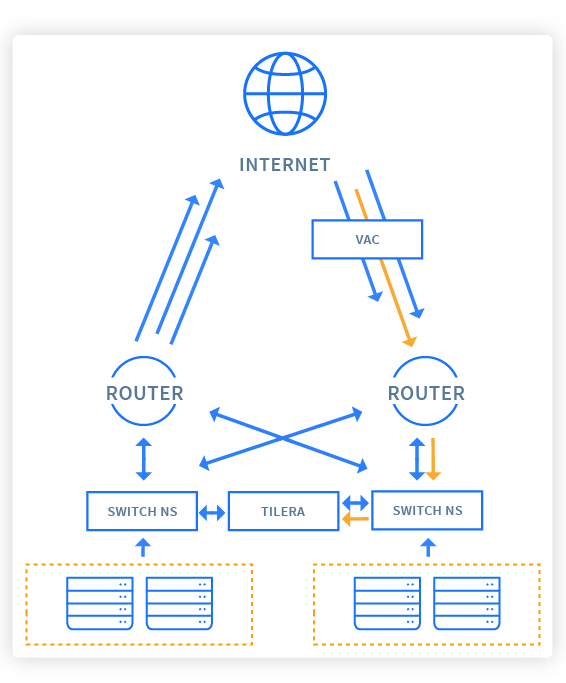
To protect your servers and services from attacks, OVHcloud offers a mitigation solution based on VAC technology - an exclusive combination of techniques to:
- Analyze all packets at high speed, in real time
- Vacuum your server's incoming traffic
- Mitigate past singling out illegitimate IP packets, while allowing legitimate ones to pass through
Anti-DDoS GAME protection
The gaming/e-sports industries are specially prone to distributed deprival-of-service attacks. Protection solutions implemented by hosting providers ofttimes accept express capacities when faced with the intensity and frequency of these attacks, peculiarly UDP flood attacks, which exploit the User Datagram Protocol (UDP) - the protocol used by the majority of games and phonation servers.
To protect these customers, we developed an Anti-DDoS protection specifically adapted to Game servers.
List of uniform games and applications:
Half-life, Team Fortress Classic, Counter-Strike i.6, Counter-Strike: Source, One-half-life Deathmatch Classic, Half-life ii, One-half-life 2: Deathmatch, Day of Defeat, Day of Defeat : Source, Left four Dead, Left 4 Dead two, Team Fortress 2, Counter-Strike : Global Offensive, Garry's Mod, Grand Theft Auto, San Andreas Multiplayer SA:MP, Multi Theft Car San Andreas MTA:SA, TrackMania (+ TCP protocol), TrackMania 2 (+ TCP protocol), ShootMania Storm (+ TCP protocol), Minecraft pocket edition, Minecraft ARK : Survival Evolved, RUST, Teamspeak, Mumble.
Anti-DDoS protection tailored to your game
To provide the best possible protection against attacks, the OVH engineers analyzed how the nigh pop gaming platforms (Counter Strike, TeamFortress, Minecraft) and communication modules (TeamSpeak and Mumble) operate. In a lab and by looking at existent user tests, they studied the vulnerabilities of these applications and documented the diverse set on strategies. This reverse engineering enabled them to provide a tailored response to each large game family: for each family, they adult a contour - or a group of predefined rules - that tin can be deployed by the user in one click to filter illegitimate traffic flowing in and out of the UDP ports.
2-way mitigation: a filter on entry and exit
For every blazon of attack, we've built a specific response closely integrated to the servers and straight integrated inside the Tilera hardware. The large innovation is a filter that analyzes the incoming and outgoing traffic to amend identify legitimate requests. It's capable of distinguishing real clients connecting to the car from harmful attacks. Anti-DDoS GAME therefore also plays the part of a cache and a filter for TCP/IP and UDP packets.
A router located side by side to the auto analyzes packets. This router treats every hosted game as a special instance. For example, the router acts as a cache to relieve the router of useless requests.
Anti-DDoS Solution
The OVH network is capable of absorbing all attacks. With an additional 17+ Tbps of capacity maintained in relation to the standard usage of all our customers, the OVH network is able to withstand, vacuum, and mitigate a high number of attacks. During the mitigation procedure, spread across nine data centers and 3 continents, the attack vacuuming is reinforced. All our customers' SLAs are counterbalanced and guaranteed in this way, and the service will never be disrupted.
Analyze
Nosotros use the netflow sent by the routers and analyzed by our detection solutions to identify attacks. Each router sends a summary of i/2000 of traffic in real time. Our solution analyzes this summary and compares it to the attack signatures. If the comparison is positive, the mitigation is set up in a matter of seconds.
The signatures analyzed are based on the traffic thresholds in "packets per second" (Pps, Kpps, Mpps, Gpps) or "bytes per second" (Bps, Kbps, Mbps, Gbps) on a certain package type such equally:
- DNS
- CMP
- IP Fragment
- IP Zero
- IP Private
- TCP NULL
- TCP RST
- TCP SYN
- TCP ACK
- UDP
Traffic Vacuum
The principle of DDoS attacks is to overload services. Sometimes the provider's entire network is incapable of handling the load. Thanks to our 17+ Tbps network capacity, OVH infrastructure can absorb a very high quantity of traffic during attacks, much more than the services offered past competitors.
When the attack is global, the mitigation services, replicated in viii OVH data centers across three continents, actuate simultaneously to combine their ability and absorb the traffic. Their total capacity mitigation is more than 4 Tbps. Other customers and services volition not be affected at all.
Mitigate
Past default, all OVH servers are equipped with automated DDoS attack mitigation that activates in the event of an assault (reactive mitigation). Customers besides have access to permanent mitigation (permanent rules) too as Network Firewall configuration.
Mitigation is a term employed to pattern the means and measures in place to reduce the negative effects of a DDoS attack. Mitigation At OVH consists of filtering illegitimate traffic and hoovering it upward with our the VAC technology , while letting legitimate packets go through.
The VAC consists of multiple devices, each with a specific function to block 1 or more types of attack (DDoS, Flood, etc.). Depending on the attack, i or more defense strategies may exist put in place on each VAC device.
Actions carried out on the Pre-Firewall
- Fragment UDP
- Size of packets
- Say-so of TCP, UDP, ICMP, GRE protocols
- Blocking all other protocols
Deportment carried out on the Network Firewall
- Authorize/block an IP or a sub-network of IPs
- Authorize/block a protocol
- IP (all protocols)
- TCP
- UDP
- ICMP
- GRE
- Authorize/block a port or TCP/UDP port interval
- Authorize/cake SYN/TCPs
- Authorize/block all packets except SYN/TCPs
Deportment carried out on the Shield
- Malformed IP header
- Incorrect IP checksum
- Incorrect UDP checksum
- ICMP limitation
- Incorrectly fragmented UDP datagram
- DNS amp
Actions carried out on the Armor
- Malformed IP header
- Incomplete fragment
- Incorrect IP checksum
- Duplicated fragment
- Fragment too long
- IP/TCP/UDP/ICMP bundle likewise long
- Incorrect TCP/UDP checksum
- Invalid TCP flags
- Invalid sequence number
- Zombie detection
- TCP SYN hallmark
- DNS authentication
- Badly formed DNS asking
- DNS limitation
Pre-firewall
The Pre-Firewall is based on Arista 7508R, which is able to connect 288 100 1000 ports, i.e. 28.8 Tbps of advice capacity. VRF isolation and so allows the traffic to be routed within successive stages.
| Model | Arista 7508R |
| Supervision card | 2x DCS-7500-SUP2 |
| Processor | Multicore x86 |
| Frequency | 2.13 GHz |
| RAM | 32 GB |
| Fabric | DCS-7508R-FM |
| Service cards | 2x 7500R-36CQ |
| Capacity | 28.8 Tbps / 34.5 Bpps |
| Full pre-firewall chapters | 1.2 Tbps / ane.8 Bpps |
Network Firewall
The Network Firewall is composed of vRouters executing OVH-developed code, enabling all traffic to be classified so that rules tin exist practical (access-lists).
| Processor | 2x1697v4 |
| RAM | 64 GB DD4 ECC |
| Network cards | 2x ConnectX-four 2x 100 Gbps |
| Capacity | 200 Gbps / 100 Mpps |
| Number per VAC | 3 |
Shield
Shield is an OVHcloud-developed software solution that runs on vRouters. Its purpose is to mitigate known attacks, mainly those that work via amplification (DNS Amp, NTP Amp)
| Processor | 2x1697v4 |
| RAM | 64 GB DD4 ECC |
| Network cards | 2x ConnectX-iv 2x 100 Gbps |
| Chapters | 200 Gbps / 100 Mpps |
| Number per VAC | 3 |
Armor
Armor is the most advanced VAC software solution, designed to mitigate advanced persistent attacks. It runs on vRouters with FPGA cards in order to reduce the CPU load on part of the processing and obtain the best operation levels on complex algorithms.
| Processor | 2x1697v4 |
| RAM | 64 GB DD4 ECC |
| Network cards | 2x ConnectX-4 2x 100 Gbps |
| FPGA | XUSP3S with 4x 100 Gbps |
| Chapters | 200 Gbps / 100 Mpps |
| Number per VAC | 3 |
Learn more near OVH Points of Presence (PoPs)
Anti-DDoS Resources
Recommended forms of protection
| Your situation | Our advice |
| Your state of affairs | Our advice |
| OVHcloud Network Firewall settings | Ensure that just authorized and necessary ports are enabled on your server; don't miss whatever port or service to avoid disconnection due to incorrect settings. Utilize the Network Firewall interface on your OVHcloud Control Console or API. |
| Configuration of your server settings | Adjust your server's IP settings past customizing the TCP, UDP values in/proc of your Linux. |
| Public and private network | If your infrastructure consists of several servers, use vRack for all services between your servers. |
| Exam the permanent mitigation | You can activate mitigation on your server and thus verify that it'due south working correctly under the VAC. That way, y'all won't go any nasty surprises on the day you lot become attacked. |
| In the event of an attack | Follow the situation via the Control Panel to confirm when it has been restored. By default, the mitigation volition stop 26 hrs after the outset of the assault. |
| Prepare a business organization contingency plan | If possible, apply our three data centers to duplicate your infrastructure geographically and devise a service continuity plan in accelerate. |
Customer control panel
Simple control of your anti-DDoS security
Whether you've opted for standard or a more sophisticated mitigation (as office of the OVH Extended features option), y'all can accept full control of your strategies and firewall settings via the graphical user interface in your Control Panel.
Oversee the set on monitoring process
Your Command Panel likewise allows y'all to monitor attacks (status and intensity) and to have total control of the deportment.
RESTful API
In addition to the Control Panel which enables y'all to control your mitigation strategies and Network Firewall on a daily basis, OVH offers customers a comprehensive and secure API that lists all possible deportment.
A clear and documented RESTful API, ideal for developers.
The OVH RESTful API allows y'all to list all the assistants actions on your network security, on i page and by category. Each role has a description, action buttons, and for developers, examples of code for integrating these functions into your scripts. In improver to the quick command of your security services, the OVH RESTful API opens upwardly wide possibilities to automate sure tasks, integrate them into your development, and update the configuration of your app settings and policies.
Click hither to access the OVH API
Glossary
| Anti-DDoS | Set of calculating techniques aimed at protecting online services from DDoS attacks |
| DDoS | Distributed DoS; The principle is the same as DoS, but with multiple points of attack |
| DoS | Deprival of service; a blazon of cyber-set on |
| Mitigation | The human activity of identifying, selecting the appropriate filtration and isolation, and neutralizing the furnishings of a cyber-set on |
| SLA | Service Level Agreement; the obligations of the supplier in terms of quality and availability of services |
| Synflood or SYN Alluvion | A cyber-attack carried out on the basis of SYN requests |
| VAC |
FAQ
The Anti-DDoS protection is included for free with all servers, no matter the elapsing of your contract.
We provide free, 24/7 mitigation to 100% of OVH infrastructures and servers. The just way to protect our customers is to protect all of them. This is why all of our servers must be protected.
If a specific policy has not been selected via the API or the Command Panel, OVH will utilise standard mitigation rules for your server. This is done in an automatic and escalating way (increasingly restrictive until isolation of the results).
All policies have been gear up upwardly to protect the attacked ports by leaving other ports open. This preserves the SLA of servers on the other ports.
The professional employ option allows you to proactively cull which policies will be applied in the event of an active set on (at any time). If the policy selected by the customer is not sufficient, an OVH policy volition take over until the attack is stabilized; this allows the client to decide which is the best solution before OVH decides for them.
hedlundmicketionath.blogspot.com
Source: https://us.ovhcloud.com/products/security/anti-ddos
0 Response to "A Reflective Attack Can Be Increased in Intensity by Combining It With What Type of Attack?"
Post a Comment